- Email: info@ciamagnifier.om
- Phone: +968 99700719
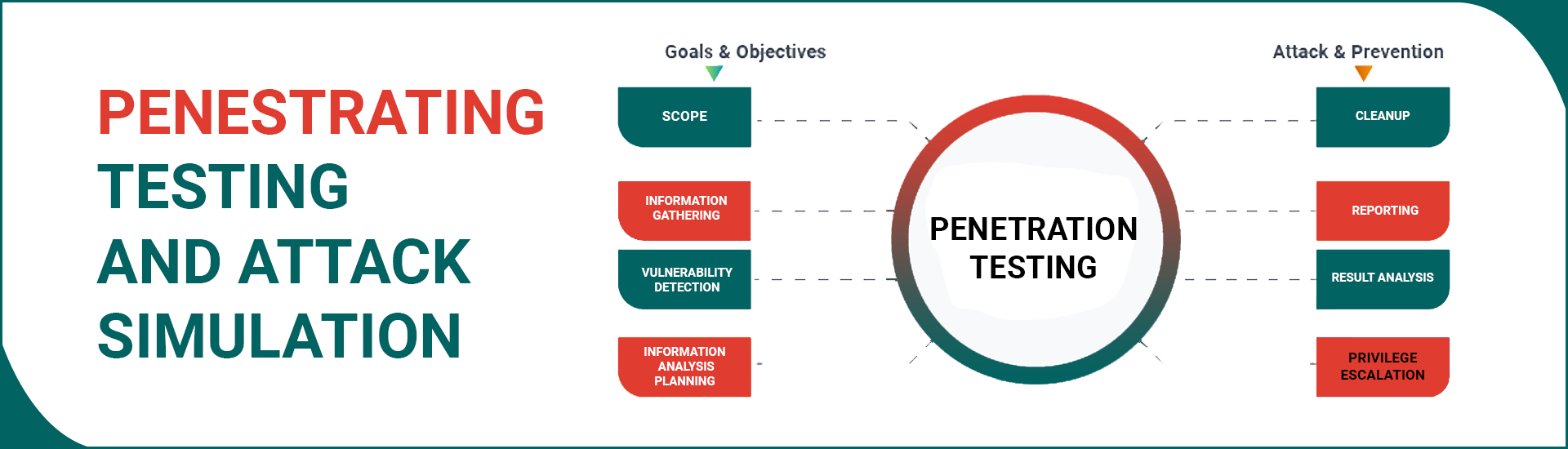
The fast-paced evolution of technologies for changing landscape of IT and Cyber-systems has paved way for more complex security challenges globally. CIA Magnifier provides independent Penetration Testing and Cyber-attack Simulation services to evaluate internal and external cyber defense the organization has deployed as per International Regulatory/legal bodies. These tests provide us with an in-depth assessment of your network/cyber security levels and aid our experts to recommend a fine-tuned system containing appropriate security policies, adequate controls, periodic review, and monitoring to raise protection against all the threats.
CIA Magnifier’s Specialized Penetration testing team is equipped with state-of-the-art attack capabilities, technology, and field expertise. They can perform simple level to complex elevated-security level cyber or system attacks to provide successful simulation, threat hunting/ recognition, and weaknesses of all sizes of organizations.
We know when a giant hacker successfully launches an attack on your system, the size of the damage will be irrecoverable data, finance, technology, and reputation-wise until or unless your readiness has been tested by our Cyberattack Simulation. Our Cyber-attack Simulation offers valuable insight into a hacker’s mind, their approach to detect unseen vulnerabilities and exploit them to their full potential. We provide you comprehensive expert services utilizing multi-faceted attack simulation using technical audits, pen tests, social engineering techniques (phishing, physical on-premises, malware, intrusion) backed with Darknet/Social Networks Research. This tests the full-readiness, strength, and maturity of your security systems, gaps/risks related information, and possible dangers to your cyber or network security.
CIA Magnifier performs focused external penetration tests to examine unidentifiable security risks which cannot be picked up by general automated tools. These External Pen testing techniques involve gathering critical information concerning networks and client systems identifying systems that are available over the internet. These available systems define our exposed attack surface as vulnerable to any anonymous IT or cyber-attacker.
CIA Magnifier performs OWASP TOP-10 based Web application security audit targeting technical web-server testing and identification of critical vulnerabilities for determining exposed attack surfaces to script kiddie or web-attackers.
This Security audit performs technical analysis of Web-based applications, server platforms, and source code for recognition of weaknesses exposing the application to immediate or later security threats, hackers, and breaches. This coordinated audit utilizes OWASP Web Security Testing Guide (WSTG), OWASP Top 10 Web Application Security Risks, and augmented tests specifically performed by our experts.
Our Web API Security Audit tests your Web API and its API server technically from the viewpoint of a professional attacker. The audit takes place under the guidance of OWASP WSTG, OWASP API Top-10 security risks, and complementing specialized tests from our team. This is to determine all probable risks and exposure to cyber-attackers/criminals.
Our OWASP Mobile Application Security Verification Standard (MASVS) governed mobile app penetration and API test make certain that all possible technical attack areas are evaluated fully to determine weaknesses and cyber-risks of our mobile apps exposed to attackers. We perform tests to determine your ranking on both levels of security performance against the two levels of security requirements outlined by MASVS, which are:
• Level 1 requires all mobile applications, and their API must offer basic protection against probable attacks.
• Level 2 requires all high-risk mobile apps such as e-banking, healthcare, and sensitive industries to meet higher security requirements, defense measures, and certifications.
Our WLAN audit examines complete WLAN Infrastructure for its security limitations, risk vectors, verification of current security measures, and compliance with industry standards. This test checks the strength of your WLAN against external attacks from an authenticated framework integrated into the network or other unauthorized channels.
Our Technical Audit of Email and Proxy infrastructure is designed to assess any technical or configuration weak spots which provide an attacker opportunity to exploit/steal/control your IT networks with the help of malicious email attachments/ suspicious download links.
CIA Magnifier performs technical audit and review of Windows 10 client (physically/virtually) or Windows Server 2016 terminal server. This audit identifies our client’s vulnerabilities in the physical, server, or network areas while reviewing protecting measures against attackers. "Centre for Information Security" (CIS) benchmarks and the Microsoft Security Baselines are used by us as standards to run, execute, and compare the test results.
Social engineering audits are crucial for information security concerning your staff and confidential information. We perform a series of audit methods in the context of information security, as well as manipulating means to pressure staff members into performing actions or disclosing confidential information. This testing takes place with the consent of the client, aimed to deliver a comprehensive report of security vulnerabilities and loopholes before an experienced attacker can take advantage of them. These Social Engineering Audits provide comprehensive reporting, user tracking, and risk classification.
All our tests are either physical, phone, or computer-based, and we gain much open-source information before initiating engagement via online information mediums. We use different techniques like:
• Spear Phishing Email campaigns
• Spear Phishing in combination with the simulated misuse of the endpoint
• Phone-based social engineering attack involving Caller ID, SMS spoofing, and Voice Phishing
• USB devices with simulated malware dispersed to trace who uses them